-
Apr 24 20240Guy Fawkes Anonymous Cybersecurity Experts: ‘The Ultimate Online Safety Guide for Senior Citizens’. While you think of technology’s benefits to overcoming some of the challenges of aging – mobility, making friends, managing healthcare and reducing errands – it’s easy to fall prey to its dark side. Without realizing it, you may
-
Apr 14 20240Nivedita James Palatty Cybercrime statistics show that a minimum of 422 million individuals were impacted, according to the FBI’s internet crime records with 800,944 complaints registered in 2022. Nearly 33 billion accounts will be breached in 2023 with the cost of these breaches predicted at $ 8 trillion. This Blog Includes show The
-
Apr 12 20240Leon Geter’s TEDxCharleston talk, “By Cybersecurity Safe: Lock Your Digital Door,” likely emphasizes the importance of cybersecurity and provides insights on how individuals can protect themselves online. Geter may discuss common cyber threats, such as phishing and malware, and offer practical tips for safeguarding personal information and digital assets. He
-
Apr 12 20240Jeff Crume’s “2024 Cybersecurity Trends” likely discusses emerging trends and developments in the cybersecurity landscape anticipated for the year 2024. This could include advancements in technology, changes in threat landscape, new regulatory requirements, evolving best practices, and strategies for organizations to stay ahead of cyber threats. Without watching the video
-
Apr 12 20240Jeff Crume’s presentation titled “Cyber Attack Trends: Global Identity Crisis” likely delves into the current landscape of cyber attacks and their trends, particularly focusing on identity-related issues. Crume might discuss the rising threat of cyber attacks globally, highlighting how attackers exploit identity vulnerabilities to breach systems and networks. He may
-
Apr 06 20240By Sergiu Gatlan: Google announced a new Chrome security feature called ‘Device Bound Session Credentials’ that ties cookies to a specific device, blocking hackers from stealing and using them to hijack users’ accounts. Cookies are files that websites use to remember your browsing information and preferences and automatically log you
-
Apr 06 20240Ernestas Naprys Senior Journalist: Threat actors have come up with a new solution called Geobox that transforms the mini-computer Raspberry Pi into a Swiss-army knife type of hacking device for fraudsters and other criminals. Sold for a lifetime fee of $700 or a monthly rate of $80, the software is
-
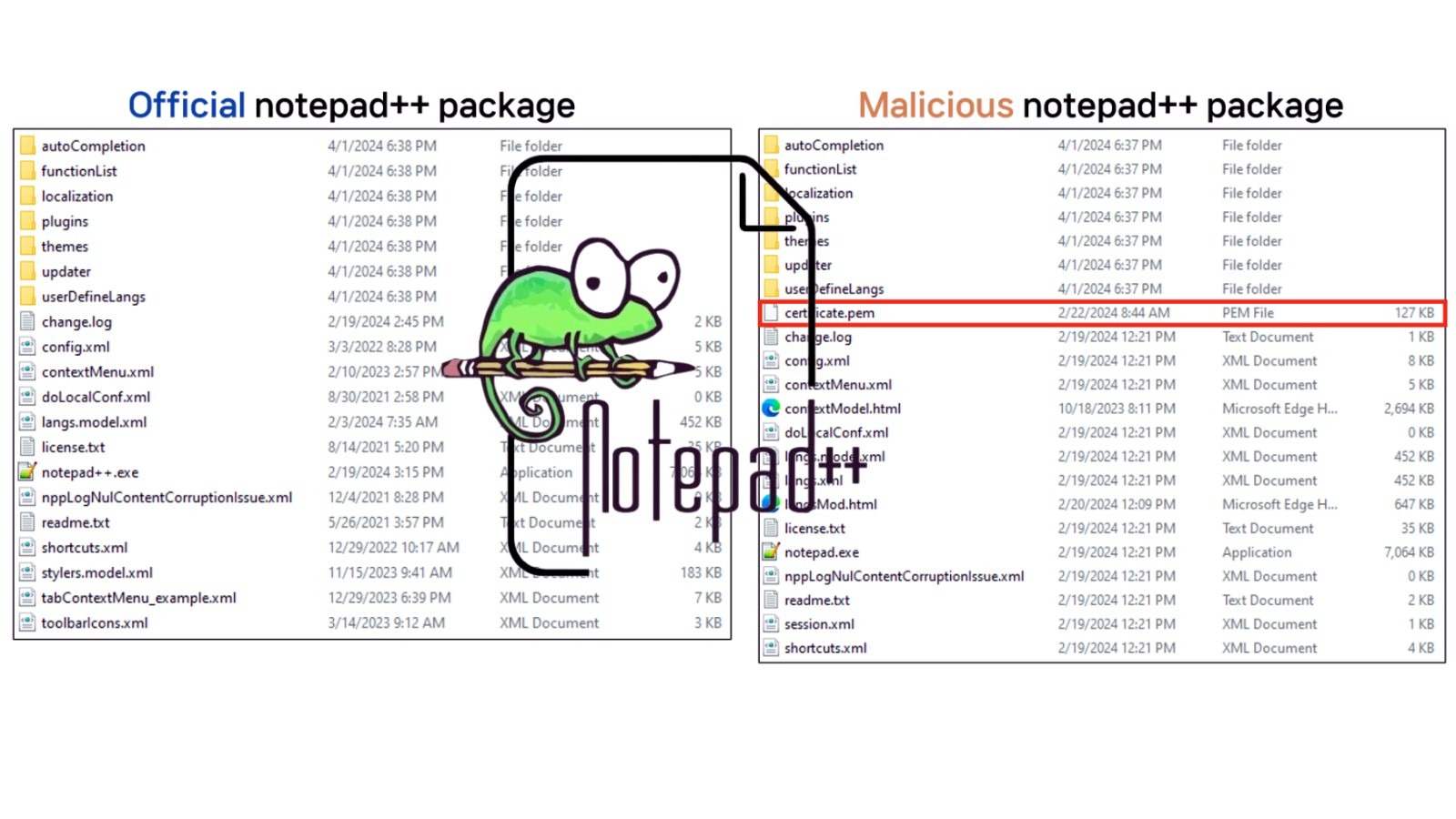
Apr 06 20240ByGuru Baran: The AhnLab Security Intelligence Center (ASEC) has detected a sophisticated cyberattack targeting users of the popular text and code editor, Notepad++. Hackers have successfully manipulated a default plugin within the Notepad++ package, potentially compromising the security of countless systems. The plugin in question, “mimeTools.dll,” is a standard component of
-
Apr 06 20240By Bill Toulas: Newly discovered HTTP/2 protocol vulnerabilities called “CONTINUATION Flood” can lead to denial of service (DoS) attacks, crashing web servers with a single TCP connection in some implementations. HTTP/2 is an update to the HTTP protocol standardized in 2015, designed to improve web performance by introducing binary framing
-
Apr 06 20240By Ryan Naraine: News analysis: SecurityWeek editor-at-large Ryan Naraine reads the CSRB report on China’s audacious Microsoft’s Exchange Online hack and isn’t at all surprised by the findings. The US government’s public documentation of Microsoft’s shoddy cybersecurity practices, lax corporate culture and untruthfulness in public communications should come as no
-
Apr 06 20240SAMIR BOUSSEADEN•MIKA AYENSON•JAKE KING: Elastic Security Labs is releasing an initial analysis of the XZ Utility backdoor, including YARA rules, osquery, and KQL searches to identify potential compromises. Key Takeaways On March 29, 2024, Andres Freund identified malicious commits to the command-line utility XZ, impacting versions 5.6.0 and 5.6.1 for
-
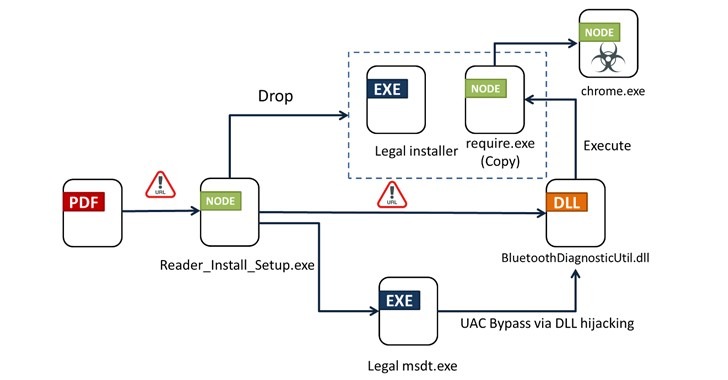
Apr 06 20240Bogus installers for Adobe Acrobat Reader are being used to distribute a new multi-functional malware dubbed Byakugan. The starting point of the attack is a PDF file written in Portuguese that, when opened, shows a blurred image and asks the victim to click on a link to download the Reader application to view