North Korean IT Workers in Western Firms Now Demanding Ransom for Stolen Data
î „
North Korean information technology (IT) workers who obtain employment under false identities in Western companies are not only stealing intellectual property, but are also stepping up by demanding ransoms in order to not leak it, marking a new twist to their financially motivated attacks.
“In some instances, fraudulent workers demanded ransom payments from their former employers after gaining insider access, a tactic not observed in earlier schemes,” Secureworks Counter Threat Unit (CTU) said in an analysis published this week. “In one case, a contractor exfiltrated proprietary data almost immediately after starting employment in mid-2024.”
The activity, the cybersecurity company added, shares similarities with a threat group it tracks as Nickel Tapestry, which is also known as Famous Chollima and UNC5267.
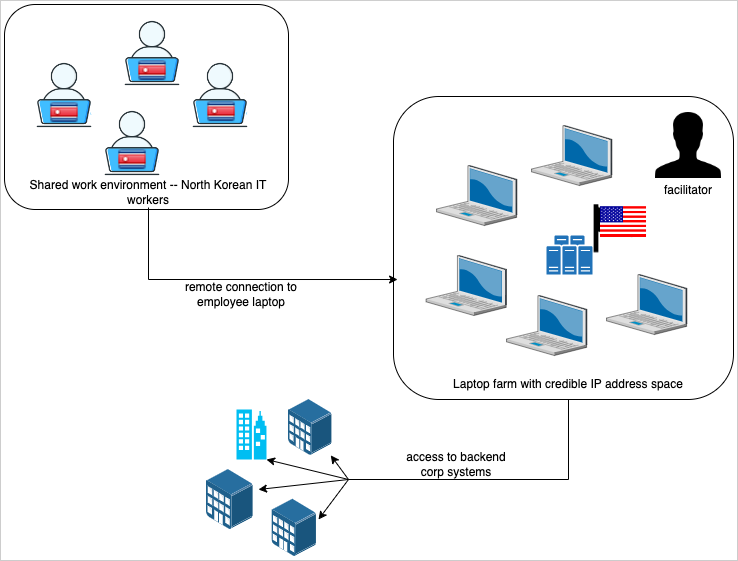
The fraudulent IT worker scheme, orchestrated with the intent to advance North Korea’s strategic and financial interests, refers to an insider threat operation that entails infiltrating companies in the West for illicit revenue generation for the sanctions-hit nation.
These North Korean workers are typically sent to countries like China and Russia, from where they pose as freelancers looking for potential job opportunities. As another option, they have also been found to steal the identities of legitimate individuals residing in the U.S. to achieve the same goals.
They are also known to request for changes to delivery addresses for company-issued laptops, often rerouting them to intermediaries at laptop farms, who are compensated for their efforts by foreign-based facilitators and are responsible for installing remote desktop software that allow the North Korean actors to connect to the computers.
What’s more, multiple contractors could end up getting hired by the same company, or, alternatively, one individual could assume several personas.
Secureworks said it has also observed cases where the fake contractors sought permission to use their own personal laptops and even caused organizations to cancel the laptop shipment entirely because they changed the delivery address while it was in transit.
“This behavior aligns with Nickel Tapestry tradecraft of attempting to avoid corporate laptops, potentially eliminating the need for an in-country facilitator and limiting access to forensic evidence,” it said. “This tactic allows the contractors to use their personal laptops to remotely access the organization’s network.”
In a sign that the threat actors are evolving and taking their activities to the next level, evidence has come to light demonstrating how a contractor whose employment was terminated by an unnamed company for poor performance resorted to sending extortion emails including ZIP attachments containing proof of stolen data.
“This shift significantly changes the risk profile associated with inadvertently hiring North Korean IT workers,” Rafe Pilling, Director of Threat Intelligence at Secureworks CTU, said in a statement. “No longer are they just after a steady paycheck, they are looking for higher sums, more quickly, through data theft and extortion, from inside the company defenses.”
To tackle the threat, organizations have been urged to be vigilant during the recruitment process, including conducting thorough identity checks, performing in-person or video interviews, and be on the lookout for attempts to re-route corporate IT equipment sent to the contractors declared home address, routing paychecks to money transfer services, and accessing the corporate network with unauthorized remote access tools.
“This escalation and the behaviors listed in the FBI alert demonstrate the calculated nature of these schemes,” Secureworks CTU said, pointing out the workers’ suspicious financial behavior and their attempts to avoid enabling video during calls.
“The emergence of ransom demands marks a notable departure from prior Nickel Tapestry schemes. However, the activity observed prior to the extortion aligns with previous schemes involving North Korean workers.”