Cyber attacks: What to do if you fear your personal information has been stolen
In recent weeks, some of the UK’s best-known brands and retailers have suffered cyber attacks.
Marks & Spencer, the Co-op and and luxury department store Harrods have all be affected by hacks or attempted hacks, leaving customers concerned about their personal data.
On Tuesday, M&S admitted that customer personal data had been taken by hackers after the retail giant was hit by a damaging cyber attack last month.
Chief executive Stuart Machin said the data had been accessed due to the “sophisticated nature of the incident†but stressed that this does not include payment or card details, or account passwords.
M&S has struggled to grapple with the fallout of the hack and retail experts have said it is likely to lead to a significant profit hit.
Here’s what to do if you are worried you’re worried about the recent cyber-attacks:
What should you do if you are concerned your information has been accessed?
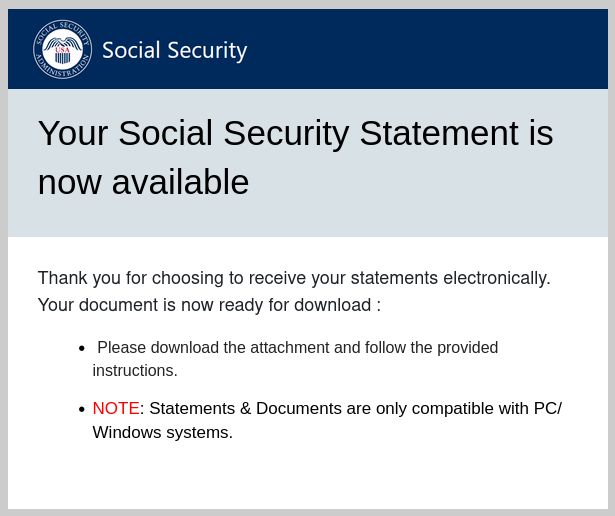
There’s no evidence stolen information from the recent cyber attacks as been shared, but consumer group Which? advises that it is wise to be cautious with any unsolicited emails or phone calls in the coming weeks.
It says if you suspect an email might be a scammer, to avoid clicking on links or downloading any attachments.
People are also warned to be cautious if your bank contacts you out of the blue, and to remember a bank will never ask for your pin, entire security number or password.
It also urges people to never reveal your full password, login details or account numbers and to instead hang up and call the company from their official phone number.
Though no passwords were lost in the cyber-attacks, M&S has advised customers to reset their passwords for “extra peace of mindâ€.
How to stay safe against cyber attacks
Co-op and M&S both suffered ransomware attacks, which is a type of virus that encrypts files on your computer or locks up its system. Hackers will then demand a ransom to give you access back.
According to a report, hackers who targeted Marks & Spencer and the Co-op tricked IT workers to gain access into their companies systems.
To protect yourself, don’t download attachments you haven’t been expecting or click links asking for personal details. Always keep your computer software updated and only download things from trusted sources.
Which? also advises people to set up a restore point on your device incase it is compromised so it can be restored from safe mode.
You should be able to do this by searching ‘â€create a restore point†on your device.
It is also advised to get a quality antivirus software for the best protection.
What data was accessed in the M&S and Co-op attack?
Marks & Spencer has revealed that customer personal data has been taken by hackers in a recent cyber attacks.
Chief executive Stuart Machin said the data had been accessed but stressed that this does not include payment or card details, or account passwords.
The high street chain did not say how many customers had been affected.
The Co-op has also apologised to customers after hackers accessed and extracted members’ personal data, such as names and contact details, while it too has suffered availability problems as a result of the attack.
Customers’ passwords and useable card details were not taken from either retailer.